Enhancing Cloud Security: A Case Study at a Major Financial Institution
Recently, our team had the opportunity to work on a project for a prominent financial institution, specifically for the IT services entity that caters to all other branches within the organization. Our primary focus was securing the public cloud infrastructure, with a particular emphasis on AWS, where our expertise lies.
Challenges in Multi-Cloud Environments
Working within a large organization with multiple entities often brings about challenges in standardization and centralization. It's not uncommon to encounter various tools performing similar functions across different teams. To streamline operations and enhance efficiency, there arose a need to centralize tasks and leverage agnostic tools for ease of management.
Centralizing Logs and Alerts
One critical aspect of our project was the centralization of different types of logs and alerts within AWS, making them readily available to the Security Operations Center (SOC). This included infrastructure logs such as VPC flow logs, findings from native AWS security tools like GuardDuty and Inspector, as well as API call logs recorded by CloudTrail.
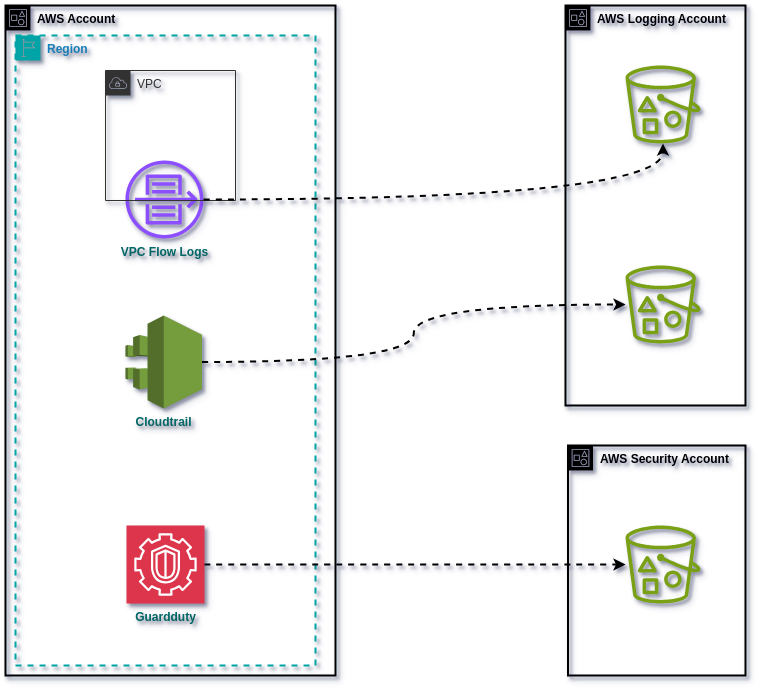
Enriching GuardDuty Alerts
GuardDuty, being a detection service, plays a vital role in identifying potential threats. However, to enable a swift response from the SOC, it was essential to enrich these alerts with additional information about the threatened environment. To achieve this, we implemented a solution using AWS EventBridge and AWS Lambda.
Through EventBridge, we monitored all GuardDuty alerts, triggering a Lambda function that enriched the alerts with crucial details such as the entity to which the threatened environment belongs and the appropriate contacts to notify. This information was retrieved through API calls made by the Lambda function to the management account.
Once enriched, these alerts were deposited into an S3 bucket, readily accessible to the SOC for further analysis and action. This centralization of logs and alerts not only streamlines the incident response process but also provides the SOC with comprehensive insights into potential threats, enabling them to take proactive measures to mitigate risks effectively.

Integrating with Azure Sentinel
At the heart of our endeavor was the need to seamlessly integrate AWS security alerts and logs with Azure Sentinel, a powerful cloud-native security information and event management (SIEM) system. Microsoft provides a connector to facilitate this integration, enabling the SOC to effortlessly ingest various types of alerts from AWS, including VPC flow logs, GuardDuty findings, and CloudTrail records.
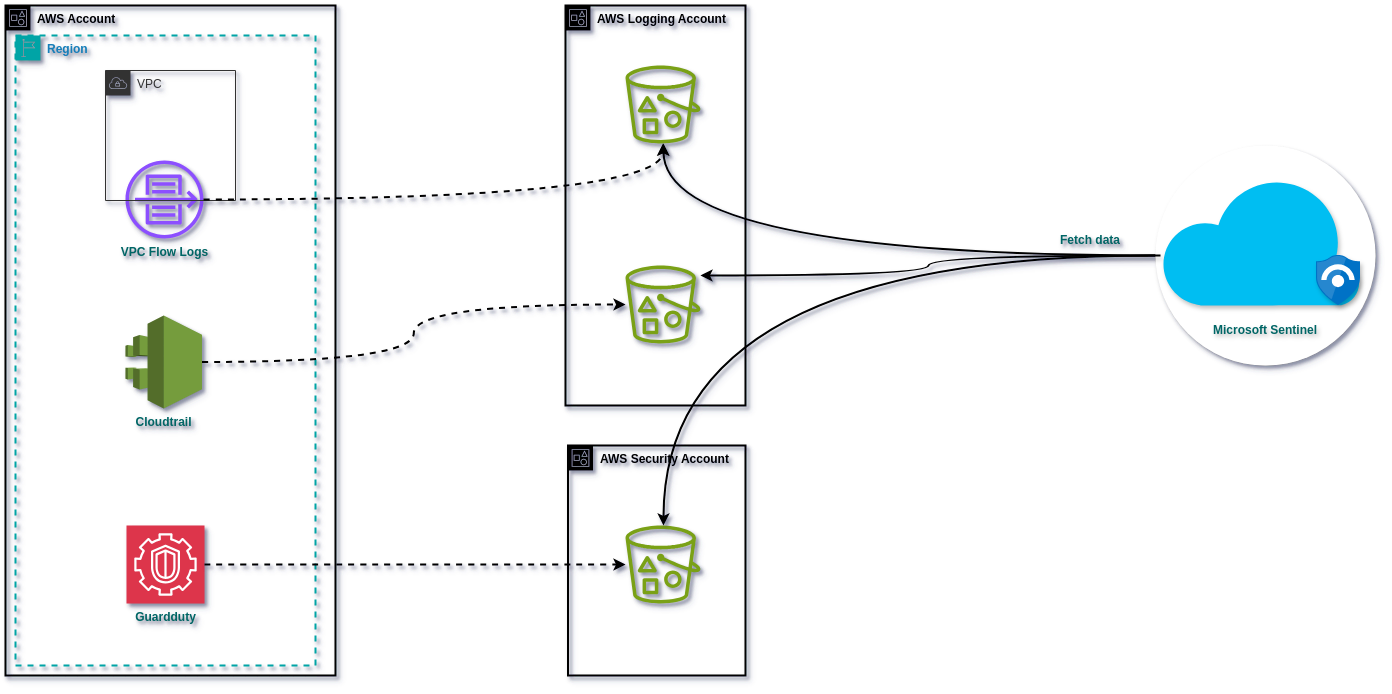
Conclusion
This project demonstrates the power of collaboration and interoperability in enhancing cloud security. By bridging AWS and Azure Sentinel, we have empowered the SOC to proactively monitor, analyze, and respond to security threats across diverse cloud platforms, ultimately safeguarding the organization's digital assets and ensuring business continuity.